
Securing the 5G Era
The first 5G radio networks are now live
Securing the 5G era remains a key priority for the industry
The purpose is to be faster, more reliable and manage the scale of devices predicted for the Mobile Internet of Things (MIoT). Enabling the digital transformation of our society, business processes and manufacturing.
To enable this, 5G will deliver multi-network slicing, multi-level of services and multi-connectivity network capabilities. To allow the required flexibility, agility and economies of scale these technologies will be delivered via virtual and containerised environments. This is a revolutionary way of working for the industry.
The fifth generation mobile telecommunication system aims to deliver fundamental upgrades:

Enhanced mobile broadband
Massive machine-type communications

Ultra-reliable and low latency communications
5G has designed in security controls to address many of the threats faced in today’s 4G/3G/2G networks. These controls include new mutual authentication capabilities, enhanced subscriber identity protection, and additional security mechanisms. 5G offers the mobile industry an unprecedented opportunity to uplift network and service security levels.
5G provides preventative measures to limit the impact to known threats, but the adoption of new network technologies introduces potential new threats for the industry to manage.
5G era security controls and their limitations:
Secure by design
5G standards development has adopted ‘Secure by Design’ principles, leading to:
- Use of Mutual Authentication
Confirming sender and receiver have an established trust and the end-to-end relationship is secured
- A presumed “open” network
Removing any assumption of safety from overlaid product(s) or process(es)
- An acknowledgment that all links could be tapped
Mandating encryption of inter/intra-network traffic, ensuring the encrypted information is worthless when intercepted
Although this is common practice in solutions for other services, such as on-line banking, it is a major paradigm shift to existing mobile telecommunications practices. As a consequence, 5G networks should afford the consumer more protection than existing 4G/3G/2G networks.
5G deployment models
The 5G standards describe a number of implementation models. Although there are plans to deploy at least 5 additional options in the future, the only option currently being deployed is the so-called non-standalone (NSA) mode, more precisely referred to as EN-DC. This is where 5G base stations are integrated with an existing 4G network working in tandem with LTE base stations and connected to the LTE Core, relying on the measures and protections that the LTE core provides.
The next phase of 5G deployment will likely be Stand Alone (SA) mode*, more precisely SA‑NR, consisting of 5G new radio network (NR) connected to a 5G core network (5GC). The change to a 5G Core will allow the full security features of 5G specifications to be realised. Although it is recognised that new paradigms (cloud native, service-based architecture) will introduce new security challenges.
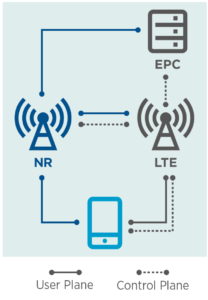
Non-Standalone (NSA) deployment
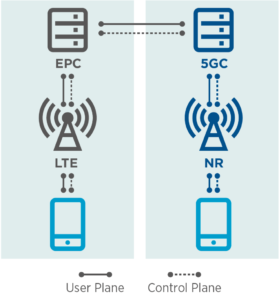
Standalone (SA) deployment
*77% of the operators we surveyed are planning to deploy SA 5G within the next three years (Source: GSMAi, 2019)
Subscriber and device protection
5G improves confidentiality and integrity of user and device data. Unlike previous generations of mobile systems 5G:
- Protects the confidentiality of the initial non-access stratum (NAS) messages between the device and the network. As a result, it is no longer possible to trace user equipment (UE) using current attack methodologies over the radio interface; protecting against man in the middle (MITM) and fake base station (Stingray/IMSI catcher) attacks.
- Introduces a protection mechanism called home control. Meaning the final device authentication to a visited network is completed after the home network has checked the authentication status of the device in the visited network. This enhancement will prevent various roaming fraud types that have hampered operators historically, and support the operator’s requirement to correctly authenticate devices to the services.
- Supports unified authentication across other access network types e.g. WLAN, allowing 5G networks to manage previously unmanaged and unsecured connections. This includes the possibility of performing a re-authentication of the UE when it moves between different access or serving networks.
- Introduces user plane integrity checking, ensuring the user traffic is not modified during transit.
- Enhances privacy protection with the use of public / private key pairs (anchor keys) to conceal the subscriber identity, and derive keys used throughout the service architecture.
As these protocols are used in the wider IT industry, their use will likely:
- Lead to a short vulnerability to exploitation timeline, and higher impact of vulnerabilities located within these protocols.
- Expand the potential pool of attackers. 4G and especially 3G core networks benefit from attackers having little experience with the propriety standards used within them.
Vulnerability reporting schemes, such as the GSMA Coordinated Vulnerability Disclosure (CVD) programme, will have to manage the increased scope of these protocols. Once located, the time to patch for relevant vulnerabilities should be short.
Network protection
Signalling data integrity
5G introduces a new network architecture element: the Security Edge Protection Proxy (SEPP). The SEPP protects the home network edge, acting as the security gateway on interconnections between the home network and visited networks.
The SEPP is designed to:
- Provide application layer security and protect against eavesdropping and replay attacks.
- Provide end-to-end authentication, integrity and confidentiality protection via signatures and encryption of all HTTP/2 roaming messages.
- Offer key management mechanisms for setting the required cryptographic keys and performing the security capability negotiation procedures.
- Perform message filtering and policing, topology hiding and validation of JSON objects; including cross-layer information checking with address information on the IP layer.
In addition, enhanced security of the international roaming services are introduced to overcome the existing security risks linked to SS7 and Diameter usage. This introduction of a dedicated security node within the 5G standards is a major improvement over the existing practices in 4G/3G/2G networks using SS7 and Diameter.
New IT protocol stack
Historically operator networks have mainly used proprietary protocols for network management. 5GC moves to an IP based protocol stack, allowing interoperability with a wider number of services and technologies in the future. The following protocols, schemas and processes will be adopted in 5GC:
- HTTP/2 over N32, replacing Diameter over the S6a reference point
- TLS as an additional layer of protection providing encrypted communication between all network functions (NF) inside a public land mobile network (PLMN)
- TCP as the transport layer protocol as replacement of the SCTP transport protocol.
- RESTful framework with OpenAPI 3.0.0 as the Interface Definition Language (IDL)
Technologies leveraged by 5G
The 5GC network architecture will be service-based, meaning that core network operations may be performed through functions outside the operator network e.g. the cloud. This is a major shift from established core network security controls, however offers the operator the opportunity to leverage virtualization technologies.
With this opportunity comes new threat vectors to contend with. Traditional virtualisation controls, including tenant and resource isolation, should be considered. Suitable isolation controls reduce the risk of data leakage and the impact of virtualisation aware malware outbreaks. Microprocessor level vulnerabilities e.g. Spectre and Meltdown have highlighted that tenancy isolation within a virtual environment is not guaranteed, as such tenants should be housed together based on security requirements e.g. do not house lower-level security tenants with high-level security tenants.
Containerisation is an OS level virtualisation technology that is gaining traction. The host OS constrains the container’s access to physical resources, such as CPU, storage and memory, so a single container cannot consume all of a host’s physical resources. Therefore reducing the impact of availability attacks against the platform. Containers often run as root and as such the ability to escape the container and access the underlying file system is possible.
Software defined networking (SDN) provides the operators the opportunity to virtualise their network flows, leading to a simplification of hardware.
All virtualisation technologies enable network segmentation and resource isolation, ensuring security and reducing the impact of successful attacks. The configuration of these services should be carried out with a secure by design ethos to ensure the protection offered is not nullified by poor management and orchestration processes (MANO).
The central control system, often the hypervisor, acts as the brain of virtualised technologies. As such the protection of this underlying technology should be high. Specific threat modelling for virtualisation aware attacks and vulnerabilities should be completed.
Cloud services
Building on virtualised services the Cloud is a key 5G enabler, 5G architecture has been designed to be cloud native as it brings elasticity and scalability. Using cloud technology can complicate the supply chain and liability chain.
According to Mobile World Live, 5G allows operators to expose rich services through the Cloud and Restful API’s. Secure coding practices should be followed ensuring data is not leaked and the code cannot be used to exploit the cloud provider or operator network.
Network slicing
Network slicing allows the operator to customise the behaviour of the network, adapting (slicing) the network to service specific use cases using the same hardware. The GSMA has defined 35 attributes that characterise a network slice in Permanent Reference Document (PRD) NG.116.
The security model for each slice should be adapted to the use case. Different levels of isolation can be envisaged spanning from a single node of the core network to fully dedicated radio access. Each isolation type must be integrated at design phase. For example a network slice for remote surgery must consider constant mutual identification and authorisation to stop MITM threats, but a slice for AR/VR content management will not require the same level of security.
Mobile IoT
Although the IoT is already prevalent in 2G/3G/4G networks the number of IoT connections are due to increase exponentially in 5G. Bigger doesn’t mean the security controls must change significantly, however they must scale. The IoT needs to be securely coded, deployed and managed throughout its lifecycle. Most IoT services share a common architecture and as such the attacks each service will be subjected to are likely to fit within three common attack scenarios:
- Attacks on the devices (endpoints) via the applications running on the device, remote attacks from the internet and via physical attack.
- Attacks on service platforms (i.e. the cloud)
- Attacks on the communications links (e.g. Cellular, WLAN, BLE air interface etc.)
On the outbound leg, IoT devices are increasingly being leveraged to launch DDoS attacks as each device creates some form of data, this linked with the volumes of devices results in significant volume-based attacks.
eSIM
An eSIM eliminates the need for a removable SIM card on the mobile device, with the data on that card instead being prepared on a remote SIM provisioning platform (SM-DP+) then downloaded in the form of an eSIM Profile via HTTPS into a secure element (eUICC) permanently embedded into the mobile device.
This eUICC, identified by a globally unique EID, is able to store many Profiles, and when a Profile is enabled, the data in that Profile is used to identify and authenticate the subscriber to the mobile network in the same way a removable SIM card would.
The system uses Public Key Infrastructure (PKI) certificates allowing the SM-DP+ and eUICC to mutually authenticate each other. All keys are generated with Perfect Forward Secrecy (PFS).
Management of eSIM Profiles on the eUICC is carried out by the End User in the consumer use case, or a remote sim provisioning platform in the M2M/IoT use case.
Artificial intelligence (AI)
Although an umbrella term for many technologies AI is expected to be widely employed in 5G networks and should benefit security. Operators should leverage Machine Learning (ML) and Deep Learning (DL) to automate threat and fraud detection.
Use of AI is particularly relevant when considering the volumes of data that 5G networks will generate. AI may be a more feasible way to mitigate previous unknown attacks in real time. AI may also be used to power self-healing networks where the system is able to identify issues and take automated action to deliver the fix.
However, this technology is also available to the attacker and AI-driven attacks are anticipated.
Legacy generations
5G is an opportunity for the mobile industry to enhance network and service security. New authentication capabilities, enhanced subscriber identity protection and additional security mechanisms will result in significant security improvements over legacy generations.
Experience has shown that 2G/3G networks make use of insecure, unmanaged protocols and are subject to fraud and threats on a regular basis. Many of these attacks have been mitigated with 4G and 5G. However, due to the backward compatibility of 4G with 3G/2G they will not disappear until the legacy technology or backward compatibility is ceased.
When defining 5G rollouts operators will have to consider how these legacy networks will impact them over time; considering how attacks could be prevented if legacy generations are either isolated or removed from the ecosystem.
GSMA 5G security activities
The GSMA is supporting the mobile security ecosystem through the following Programmes and services:
- The Fraud and Security Group (FASG) who acts as the GSMA home of 5G Security, building and sharing industry best practice on 5G fraud risks and security controls.
- The Future Network Programme supports the industry with 5G implementation guidance.
- The GSMA CVD programme successfully manages disclosures into the 5G standards, cooperating with 3GPP this research has been used to create more secure 5G standards prior to deployment.
- The GSMA IoT Security Project which develops resources specifically targeted at addressing IoT security risks.
- The Networks Group (NG) who define network architecture guidance and functionality, including SEPP configuration and network slicing templates, for 5G.
LTE to 5G comparison
| Function | LTE | 5G |
| Privacy and Integrity Cipher |
|
In addition to LTE:
|
| Authentication Key Agreement (AKA) |
|
In addition to LTE:
|
| Security Anchor Function (SEAF) or anchor key | None | Allows re-authentication of the UE when it moves between different access networks or even serving networks without having to run the full authentication. |
| Subscriber Permanent Identifier (SUPI) | Identifier sent in plaintext prior to network authentication | The Subscription Concealed Identifier (SUCI) provides a mechanism to use the home network public key to encrypt the MSIN part of the subscriber identifier (IMSI). Protecting the confidentiality of the initial non-access stratum (NAS) messages between the device and the network. |
| Home Control | None | HPMN can verify that the UE is present and requesting service from the VPMN – useful in roaming scenarios and fraud prevention. |
| Network Exposure Function (NEF) | None |
|
| Security Edge Proxy Protection | None | Protects the home network edge, acting as the security gateway on interconnections between the home network and visited networks. |
Conclusion
The purpose of 5G is to open the network up to a wider set of services and allow the mobile operators to underpin these services. It is an opportunity to protect services and consumers from many of today’s threats. 5G comes with many built-in security controls by design, developed to enhance the protection of both individual consumers and mobile networks; this is more efficient that post-deployment add-on or extras.
Advancement of technology and use of new architectures and features such as network slicing, virtualisation and cloud will introduce new threats that require new types of controls to be implemented.

